AP3 - Architecture
AP3 adds a secure computation atop the A2A protocol, so two agents can compute on their respective private data without revealing it to one another.
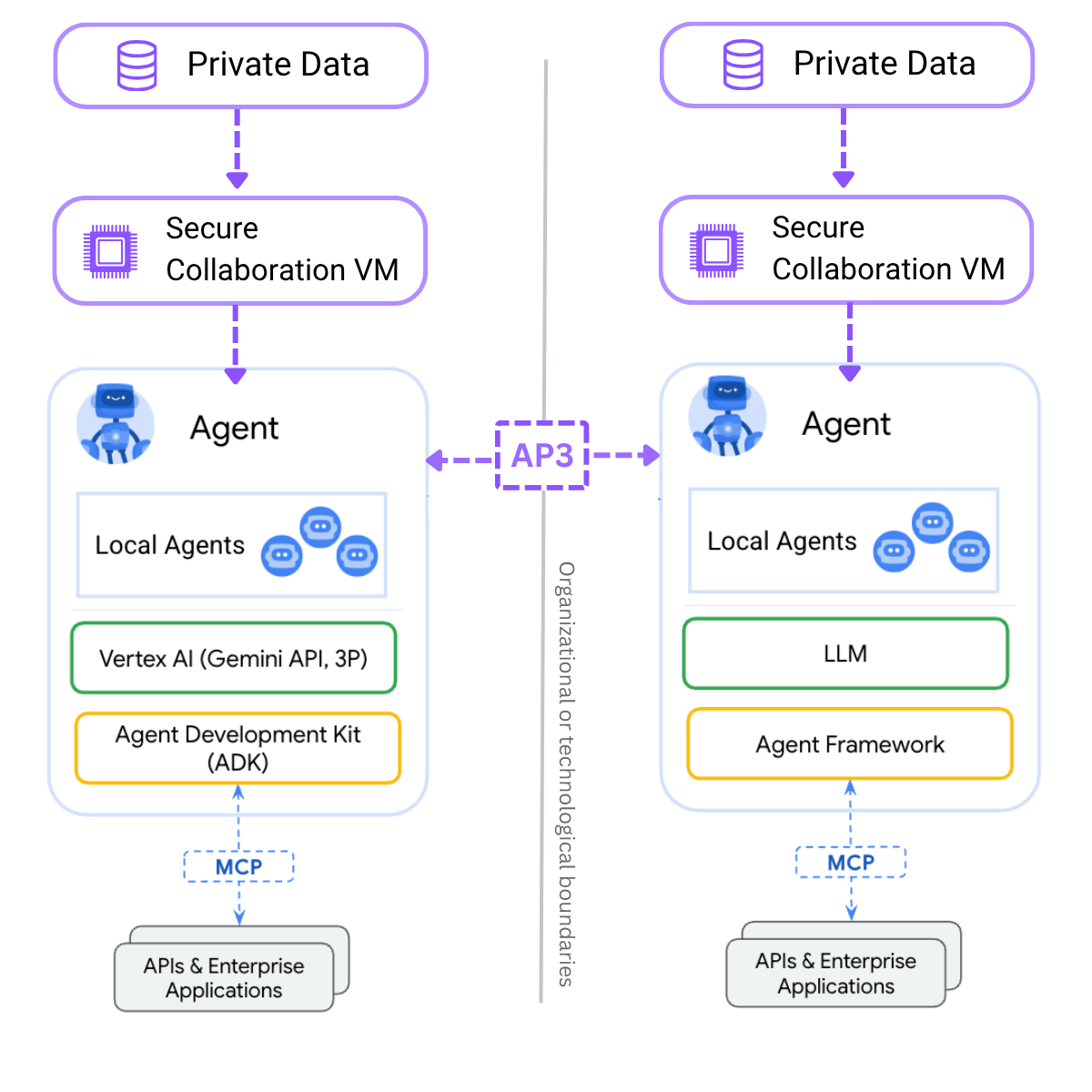
Below diagram depicts two organizations whose AI agents each sit behind a Secure Collaboration VM—connected by AP3 protocol:
- Each agent ingests its own private data, routes it through the VM, and collaborates with the peer agent to perform two‑party secure computation.
- They can share results and coordinate tasks while never exposing underlying prompts, embeddings, or user secrets
- Beneath each agent, local sub‑agents leverage an LLM stack (Vertex AI/Gemini on the left, a generic LLM on the right) and interface with internal APIs via MCP, all protected across organizational boundaries by the privacy‑preserving layer.
Core Principles
AP3 is designed around four fundamental principles:
- Privacy by Design: All computations preserve the confidentiality of private inputs through cryptographic techniques
- Verifiable Computation: Results can be cryptographically verified without revealing the computation process or inputs
- Interoperability: Built as an A2A extension, AP3 works with any compliant agent framework
- Composability: Privacy operations can be combined and chained to create complex multi-party workflows
AP3 introduces below concepts to enable privacy-preserving computation:
Sequence Diagram (example)
Let's take an example of XYZ agent who wants to find suitable partners for a blacklist of 5000 entries with 5 fields and ABC agent who wants to compute the intersection of their private sets.
sequenceDiagram
autoNumber
participant I as ABC (ap3_initiator)
participant R as XYZ (ap3_receiver)
rect rgb(240, 240, 240)
Note over I, R: 1. Agent Discovery
I->>R: GET agent card eg: (/.well-known/agent-card)
R-->>I: Returns Agent Card
end
rect rgb(240, 240, 240)
Note over I, R: 2. AP3 compatibility
I->>I: Parse Agent Card for compatibility <br/>(Roles, Commitments, Operations)<br/>
end
rect rgb(240, 240, 240)
Note over I, R: 3. Start the protocol
I->>R: Initiate privacy operation via Intent Directive
R-->>I: ACK/Validate Intent
par Operation protocol
I->>R: Encrypted data A
R->>I: Encrypted set B
end
end
rect rgb(240, 240, 240)
Note over I, R: 4. Operation Results
R->>I: Result of the operations via Result Directive
I->>I: Verify proofs and result_hash
end