AP3 - Operations
In AP3, operations are a blank canvas: it can be any mathematically expressible computation the two agents need, from a simple Boolean check to a full machine-learning inference. This means the same privacy-preserving rail can power very different business flows.
Below diagram illustrates a privacy‑preserving agent‑to‑agent workflow between two companies.
- On the left, Agent A (blue box) belongs to Company A and holds its own sensitive dataset 𝑑𝑎
- On the right, Agent B (green box) belongs to Company B and guards a different private dataset 𝑑𝑏
- Neither firm is willing—or legally allowed—to reveal its raw data outside its boundary.
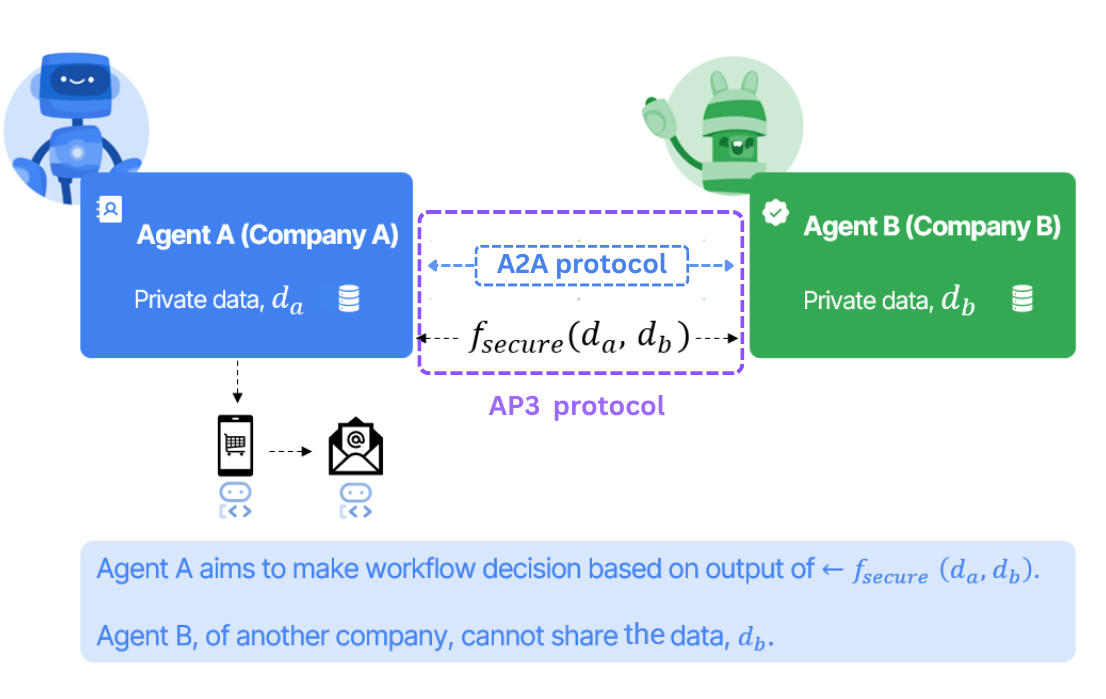
Instead of sharing data between the agents, AP3 helps in invoking a secure computation \( f_{\text{secure}}(d_a, d_b) \) between them using A2A protocol as it provides a vendor‑neutral “messaging lane” so autonomous agents can exchange requests, intermediate states, and results while respecting each organization’s authentication and access controls. Each side only sees the final output relevant to its workflow; all intermediate data stay encrypted or secret‑shared.
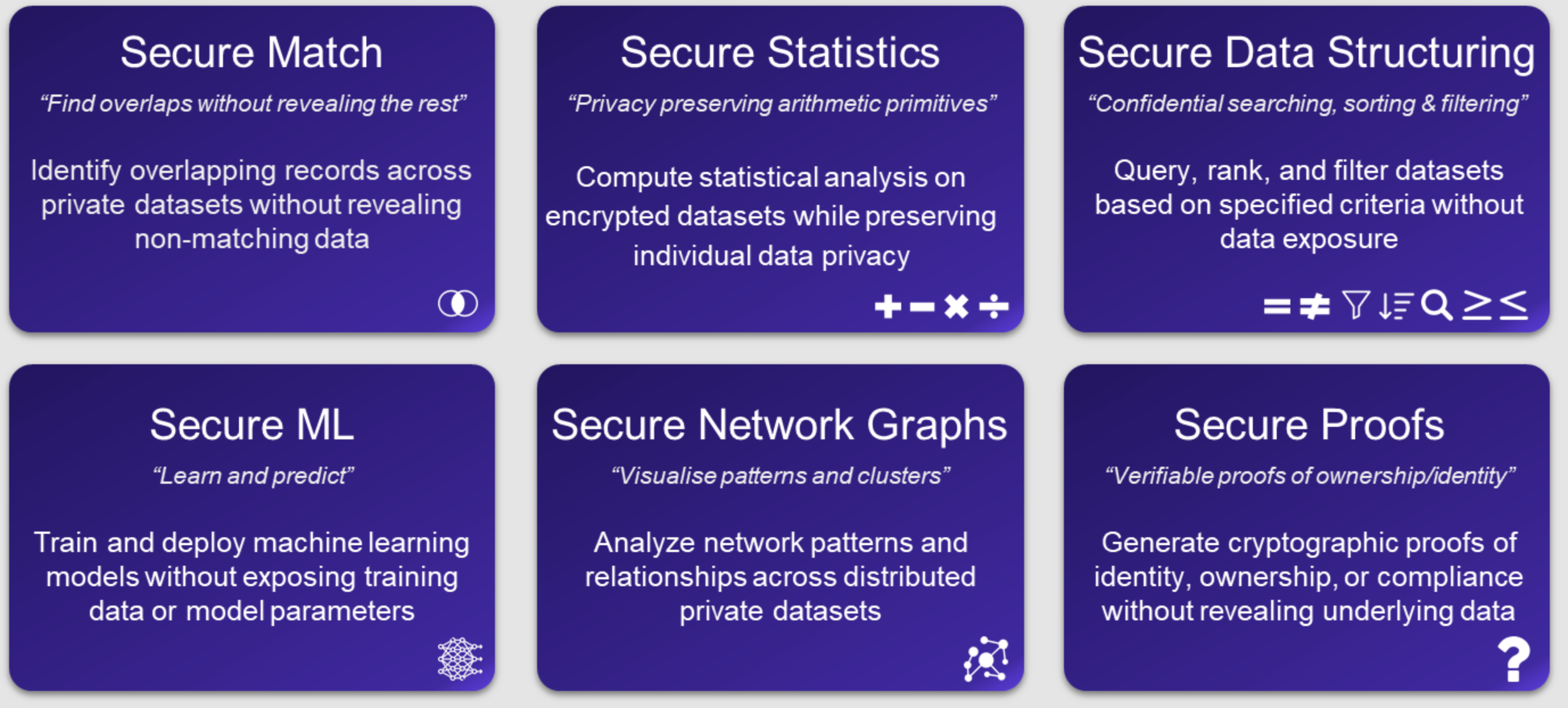
Popular, \( f_{\text{secure}}(d_a, d_b) \), functions include:
Note
All the operations are cryptographic protocols that run in the proposed Secure VM. These protocols are built and distributed as binaries for different platforms and agents load them dynamically at runtime.
Supported Operations
AP3 initially support three primary types of privacy-preserving operations:
Note
AP3 will support more operations in the future as needed and there are plans to open the protocol for defining custom functions.
Private Set Intersection (PSI)
Allows two parties to compute the intersection of their private sets without revealing elements not in the intersection.
Use Cases:
- Customer overlap analysis between companies
- Fraudulent account detection across institutions
- Supply chain partner verification
Private Information Retrieval (PIR)
Enables a party to query a database without the database owner learning what was queried.
Use Cases:
- Market research without revealing research interests
- Competitive intelligence gathering
- Secure data marketplace queries
Secure Function Evaluation (SFE)
Allows multiple parties to jointly compute a function over their private inputs without revealing the inputs.
Use Cases:
- Supply-demand matching without revealing quantities
- Performance benchmarking without revealing individual metrics
- Collaborative optimization without exposing algorithms